Telegram
Telegram founder Pavel Durov to leave $ 17 billion for his 100+ children. WLT Report
I do not know which part of this story is more crazy, but here we go anyway … Telegram founder and billionaire Pavel Durov ...
Indian Embassy Helpline Number in Iran releases Telegram links for Indian citizens
Amid growing tension in West Asia, India’s embassy in Iran has released several helpline numbers and currently created a telegram link for communication with ...
Telegram Founder Pavel Durov Allowed To Temporarily Leave France: Report
Paris: Telegram founder Pavel Durov has been allowed to temporarily leave France, where he is charged with multiple infractions linked to allegedly enabling organised ...
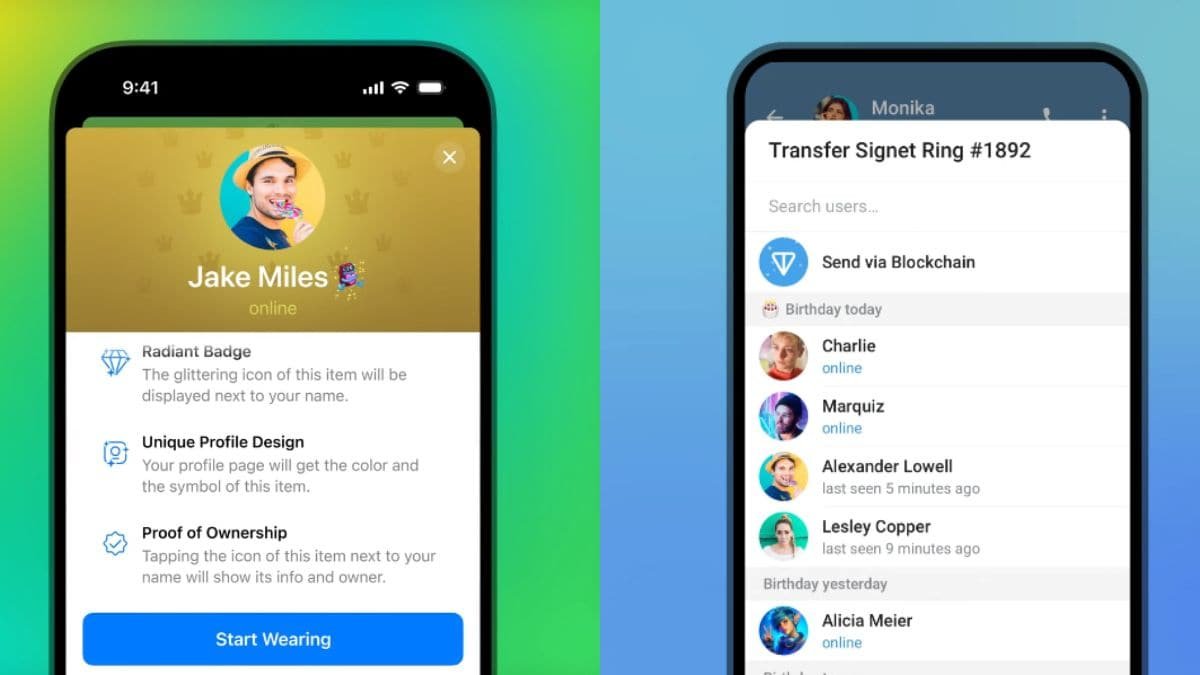
Telegram Now Lets Users Display Collectible Gifts as Status, Move Them to Blockchain and More
Telegram is rolling out six new features which may enhance the gifting experience, the company announced on Thursday. As part of the changes, users ...